THE GIBSEN METHODOLOGY
Our threat hunters and incident response teams created the GIBSEN (Graphical Information Base for Security Event Notation) methodology to simplify and standardize how incidents are described, reported, and used for training. Our cyber teams have worked with the NSA, US Cyber Command, and F2000 cyberteams, and everyone had a different model and method of organizing and representing what occurred during a cyber incident.
GIBSEN templates, artifacts, and structures leverage collaborative graphics tools like Miro and Draw.io to centralize and accelerate incident documentation and reporting. Just as MITRE ATT&CK and NIST helped standardize threats, GIBSEN will provide a shared language and methodology for your team to standardize incident reporting and resolution. The GIBSEN Methodology maps the incident reports into popular reporting models, including:
- MITRE ATT&CK Tactics®
- Mandiant Targeted Attack Lifecycle®
- Lockheed Martin Cyber Kill Chain®
 |
 |
 |
THE GIBSEN METHODOLOGY
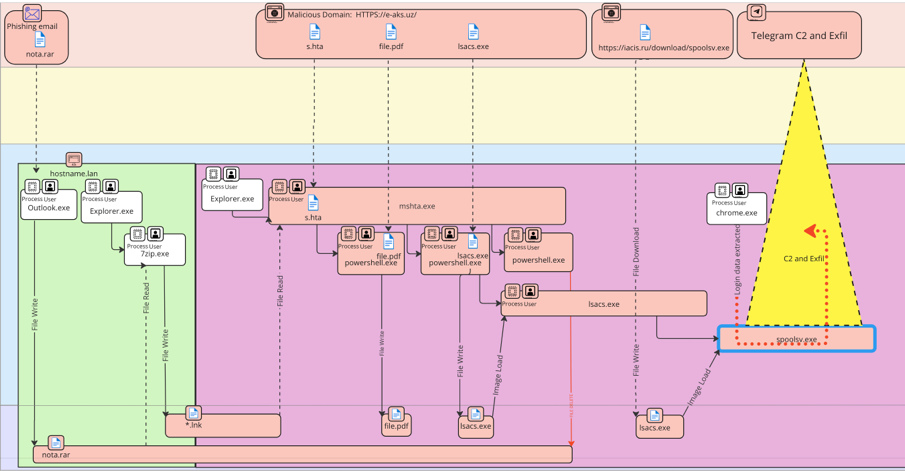
- Cyber Linga Franca - GIBSEN will create a common language and reference model for cyber incidents requiring response, remediation, and reporting. This standard model will enable teams to work faster and reduce response times.
- Training Tools - GIBSEN diagrams are valuable training tools for internal, MSSP, and supply chain partners' SecOps teams. They are concise and actionable tools for sharing threat intelligence and training people and systems.
- Auditable Evidence - Auditors and cyber insurers need evidence of care of duty, remediation, and procedural updates to sign off on compliance, manage cyber insurance requirements, and provide governance reporting.
- TTP Rules - GIBSEN diagrams provide the information required to create TTP (Tools, Techniques, and Processes) to protect against families or attacks versus individual IOCs (Incidents of Compromise).
- Governance Reporting - At the end of the day, every organization has multiple forms of governance reporting required, and the GIBSEN methodology provides a thorough, concise, and easy-to-understand way to produce reports and map them to leading threat frameworks such as MITRE, Mandiant, and Lockheed.