PRACTICE = READINESS
Cyber security and governance is a team sport, and teams must train and practice to be ready for the real thing. This is true in sports, special forces, and business. This is what Arbitr Security gives your teams new ways to train, practice, and prepare in a virtual environment for the real world of cyber threats and response. We solve four big challenges to level up your cyber readiness:
VIRTUAL INCIDENTS
Arbitr’s Virtual Cyber Incidents provide a training ground for your team to react in real time to incidents.

GIBSEN THREAT MAPS
Our GIBSEN threat incident methodology enables your team to respond to and prevent threats in your enterprise.
AUDITABLE EVIDENCE
Arbitr’s Governance Reporting Framework delivers auditable duty of care and improvement plans.
VIRTUAL CYBER INCIDENTS
Virtual Cyber Incidents (VCI) are designed to do more than “check the box.” They help your team virtually experience a cyber incident with all the challenges of the real world: incomplete information, media requests, communications demands, social traffic, policy requirements, and customer and partner inquiries, all while organizing team members spread across the globe. This is why digital tabletop exercises and incident simulations create a more beneficial, actionable, and improvement-focused program for your team. Let us show you what it is really like.
DIGITAL TABLETOP EXERCISES (DTTX)
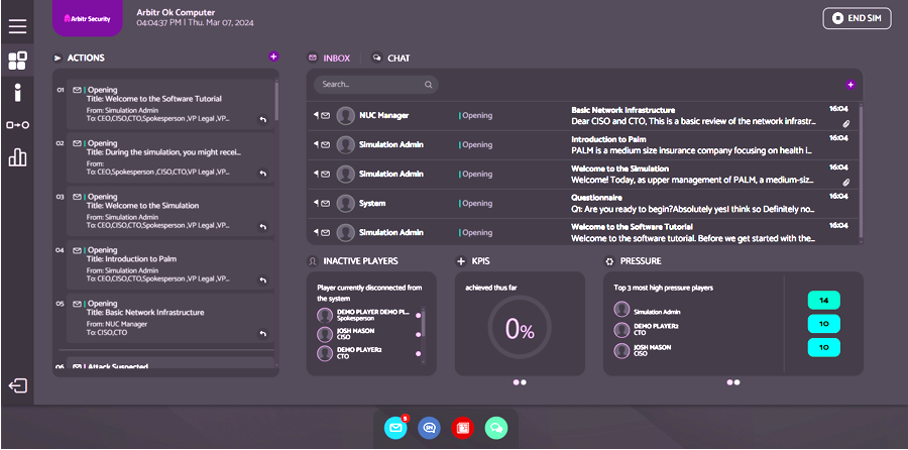
Digital tabletop exercises are a cut above their paper conversational counterparts for five human-driven reasons. As humans, we respond not just to circumstances but the types of input/media we are reacting to, the tone of communications, and the training we receive, which determines materiality for your organization. Here are three ways digital tabletop exercises (DTTX) change the game:
- Real-Time Reaction with Distributed Teams—Cyber attacks happen at the most inopportune times. People will be on planes, vacationing, unavailable, or working on the other side. We force your team to deal with these realistic scenarios.
- Digital Playback— Traditional tabletop exercises are a one-and-done event. Digital tabletop exercises can be played back, analyzed, and used to train new team members. They become a corporate asset that pays long-term dividends.
- Multi-Media Triggers– Humans react differently to texts, images, and video. Digital tabletop exercises force your teams to interact and receive information in their most and least preferred ways. This creates a better understanding of how they will work under the stress of everyday operations.
GIBSEN THREAT MANAGEMENT METHODOLOGY
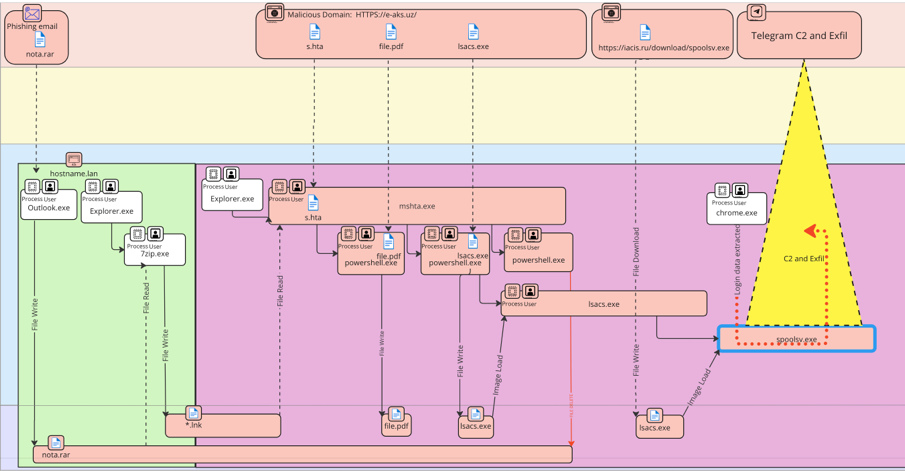
Arbitir’s Virtual Cyber Incident (VCI) exercises use the GIBSEN™ (Graphical Information Base for Security Event Notation) methodology for preparing and representing cyber incidents. The VCI will test your team against the GIBSEN incident workflow, capture your team's actions in a centralized repository, and observe how your team performs as the incident unfolds across multiple teams and technical planes of attack to understand your level of readiness and identify improvement opportunities.
SERVICES SOLUTIONS AND SERVICES

CISO EXECUTIVE PROGRAM
This program incorporates real-life experiences and skills from over 50 previous and current CISOs to give participants the confidence and capabilities required to deliver business outcomes, meet governance demands, and effectively lead cybersecurity teams in an increasingly complex cyber landscape.

SECOPS SKILLS SERIES
Becoming a SOC manager is a significant career step, and our goal is to teach you what you should know to excel in this position and lead your team. Our content and classes are conducted by people who have done the job and felt the pressure; we show you the skills required to transition from an individual contributor to a SOC manager.
CURRICULUM DEVELOPMENT
We specialize in developing cutting-edge cybersecurity curriculum tailored to the unique needs of each client. We stay ahead of the curve by constantly researching the latest threats and vulnerabilities, and we incorporate this knowledge into our training programs. Our curriculum is designed to be engaging and interactive, and we use a variety of teaching methods to ensure that learners retain the information.

TRAINING
We bring cybersecurity expertise directly to your doorstep with our on-site training programs, tailored to meet the specific needs of your organization. We also deliver engaging presentations and workshops at conferences around the world, sharing our knowledge and insights with a global audience. Our team of experienced professionals is equipped to travel to your location or present at industry events, ensuring that you receive the highest quality cybersecurity education and training, wherever you are.
GET THE LATEST NEWS
Sign up for the Arbitr ThreatOps feed with your business email.
CONTACT US
©
2023 - 2026
Arbitr Security, LLC (A CyberCodex Company)
