In a recent talk, Dmitri Alperovitch, co-founder and CTO of CrowdStrike, commented that if he spoke to a public company board, he would recommend the CISOs focus on three key metrics.
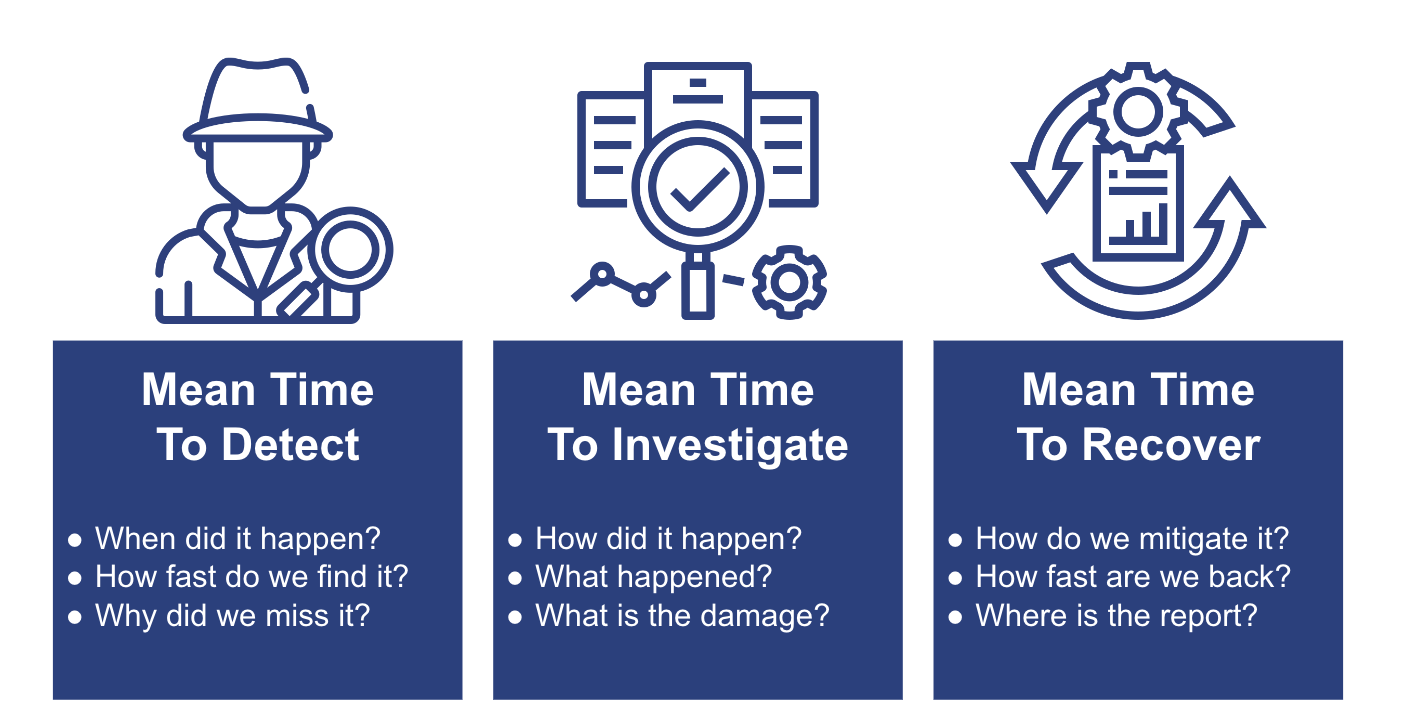 He felt these metrics focused on the core value the CISOs and security teams can share with boards, executives, and auditors to demonstrate the effectiveness of their security programs. While many other metrics could be added these get to the heart of driving continuous security improvements.
He felt these metrics focused on the core value the CISOs and security teams can share with boards, executives, and auditors to demonstrate the effectiveness of their security programs. While many other metrics could be added these get to the heart of driving continuous security improvements.
- How effective is your stack and team at finding security issues?
- How quickly can you isolate and eliminate the issue,
- How fast can you remove latent artifacts and recover operations?
- How do you create TTP algorithms to keep it from happening again?
- Can you produce executive and governance reports in time to meet regulations?
Incident Response
We have all been there. A new threat intelligence report is issued, or a new alert comes down the pipeline to your desk, and you have to start your triage process. Is this a 5-alarm fire or a manageable event? Next, you must start with a known data point and begin your hunt or investigation. Today means tracing starting with queries, and like a good detective, you have to build a timeline of the “crime” and try to trace every element and somehow assemble an end-to-end understanding of the event. This can require resources, logs, support, and data from dozens of systems across multiple teams and take weeks of research to produce a report and mitigation plan. However, the real crime is that most of this work is siloed and requires manual processes to source, document, and organize into a viable mitigation plan, build a set of TTPs to prevent similar attacks, create team assignments, and produce the required reporting. 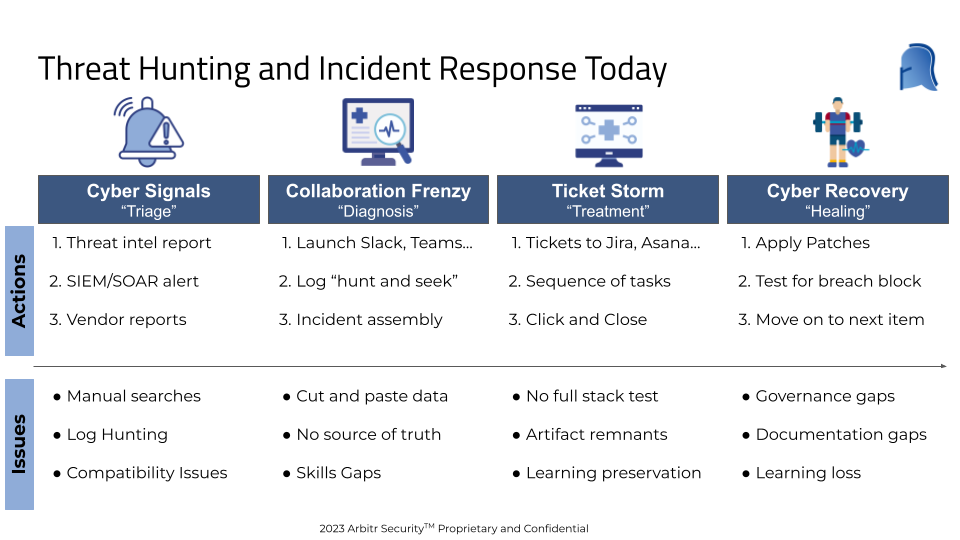
Threat Intelligence - Smart Information with Dumb Implementation
Threat Intelligence reports are genuinely the result of the best and brightest in the cybersecurity world, but the CTI reports are kind of dumb about what to do next. Like many sources of information in the world, it provides insight at a point in time and is only valuable if you can act upon that intelligence. The biggest challenge for security leaders is taking the valuable and expensive threat intelligence reports they receive, turning them into actions that improve their security posture, effectively addressing security alerts worthy of investigation, and generating reporting that meets governance requirements.
In recent reports by Jon Olstik from Enterprise Strategy Group, he highlighted critical key challenges for cyber threat intelligence (CTI) programs. ESG has defined cyber threat intelligence as “evidence-based, actionable knowledge about the hostile intentions of cyber adversaries that satisfy one or several requirements.” During his research, he noted that 72% of enterprises have a formal CTI process, and 85% of security professionals believe their CTI program requires too many manual steps. This manual slog can include cutting and pasting threat indicators into tools, correlating threat intelligence from different sources, or creating threat intelligence reports. Despite these challenges, ESG research indicates that 95% of enterprise organizations (those with more than 1,000 employees) that have a threat intelligence budget plan to increase spending on threat intelligence over the next 12 to 18 months.
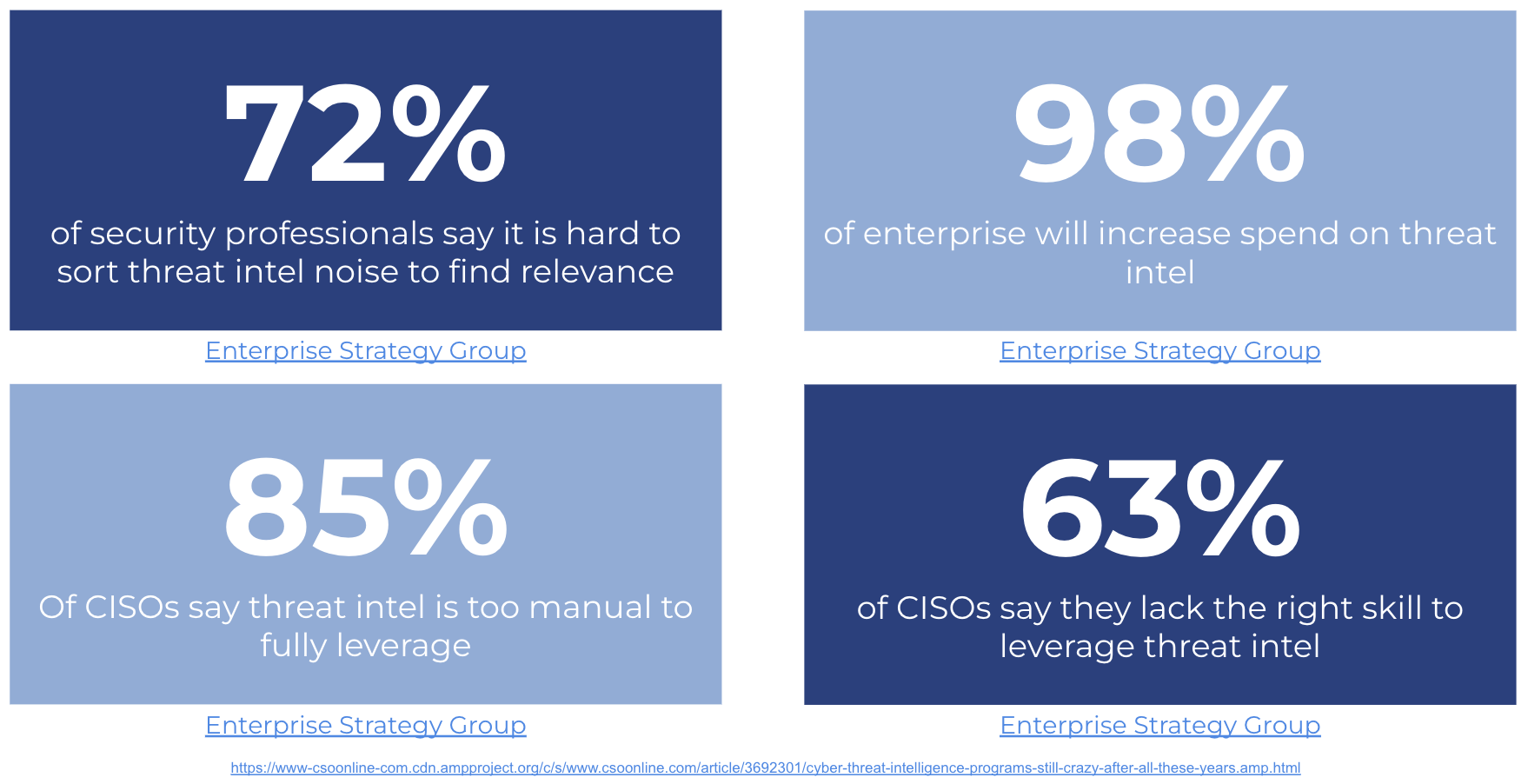
We Spend Millions on Cybersecurity Cut and Paste
The dirty secret of cyber security is that despite spending millions on cyber tools, we still have to cut and paste from disparate systems and sources to do threat hunting and incident response. This process requires hours and hours of seeking in that we hope that we find the right answers and then assemble them into a report that may never be read. This process often requires the most expensive cyber team members, consultants, or professional services teams to detect, investigate, and remediate cyber incidents.
Our ThreatOps Proposal - Never Cut and Paste Again
Suppose someone had told you when you got into cyber security that you would spend hours and hours every week cutting and pasting information from dozens of sources into a threat hunting or incident response report., Would you still get into cyber security? It would have given me pause to question my career choices. In the age of APIs, it continues to amaze us that this is the predominant way cyber professionals have to gather the information to do investigations, security engineering, team collaboration, ticket generation, and governance reporting by cutting and pasting data into other systems. This paper proposes a new way for cyber professionals to automate and accelerate these vital tasks smarter, faster, and more accurately. Our proposal is straightforward: create a new model for this process we all face every day and call it ThreatOps.
What is ThreatOps?
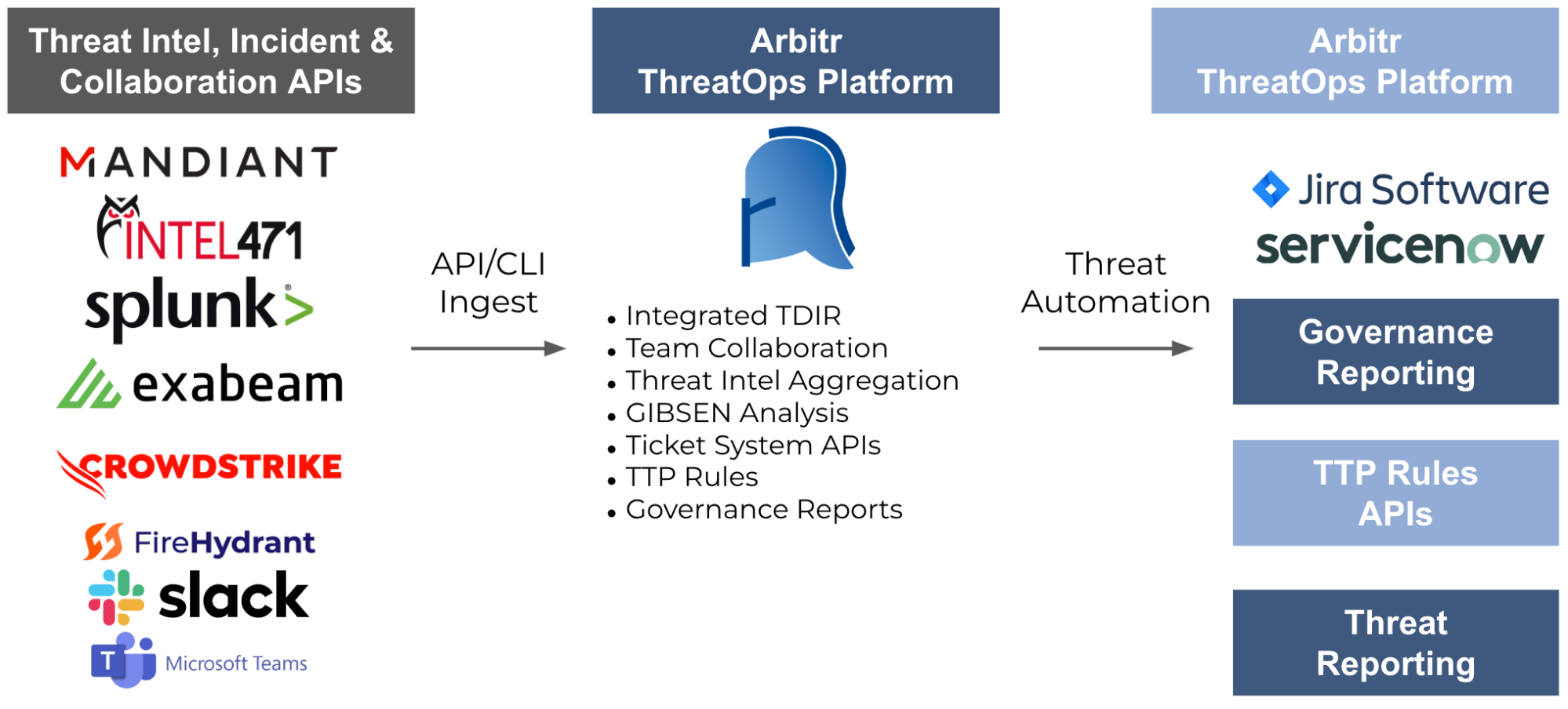
ThreatOps automates the threat hunting and incident response process to accelerate investigations and mitigations and creates TTP algorithms that improve security performance. We do this through an API-driven incident mapping tool called GIBSEN (Graphical Information Base for Security Event Notation) to standardize and map cyber incidents across technical domains to identify the incident artifacts from end to end.
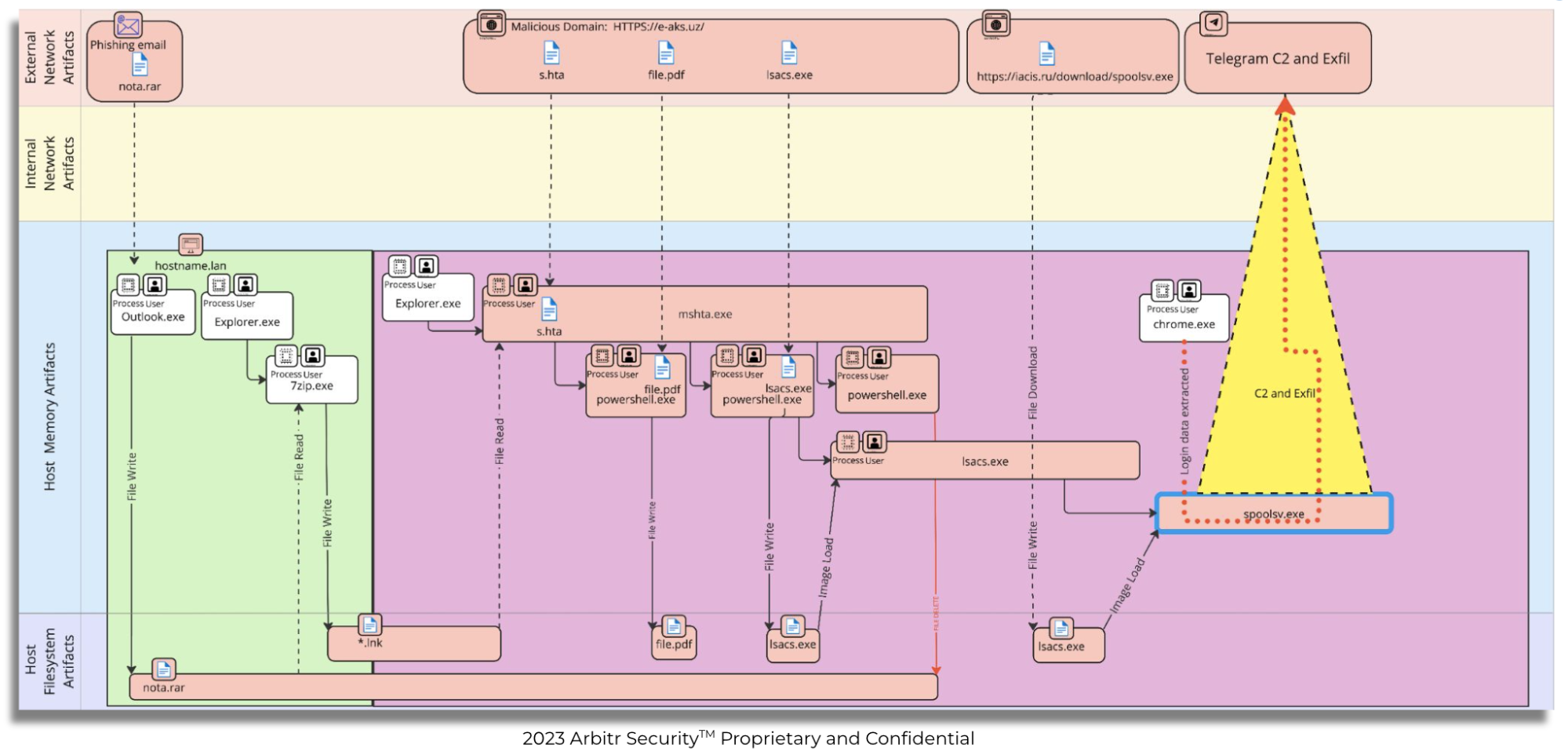
When a team starts a GIBSEN incident map, they typically have a single alert or data point, and our platform enables them to move backward and forward in time. From that first point to build an end-to-end incident map:
- Right-click to create queries, add vital information, and map your incident from end to end.
- GIBSEN leverages APIs to integrate incident signals from your cyber tools (SIEM/SOAR/XDR/Threat Intel Reports) into a graphical map for each system or network element under investigation
- GIBSEN incident maps enable teams to map incidents, identify required resources, gather required technical information via APIs, create complete mitigation plans, and integrate with ticketing systems
- GIBSEN enables the creation of dynamic TTP algorithms that provide better and more scalable security protection than static IOCs
- GIBSEN incident maps become the core resource providing governance reporting for executives, boards, auditors, insurers
We Bring Threat Intel, Tools, and Teams Together
Adding a ThreatOps capability means bringing your threat intel, systems alerts, and collaboration tools together like never before. We centralize the threat intel and incident response information from all your data sources into a single GIBSEN incident map with critical log information. Arbitr’s ThreatOps platform will help your team respond faster, fully mitigate incidents, and accelerate reporting to address shrinking governance reporting windows.
More Effective Cybersecurity with TTP Algorithms
One of the critical steps in the mitigation process is to build TTP (Tactics, Techniques, and Processes) algorithms that can be implemented in the tools of your cyber security stack to block not just the specific IOCs (Indicators of Compromise) reported but the entire family of similar attacks. Threat actors reuse the same attack techniques with minor variations to circumnavigate published IOCs. Arbitir’s GIBSEN incident maps provide a simple and effective way to create dynamic TTPs that make your tool detection more effective and prevent attacks that are quickly bypassed via static IOCs.

Faster Threat Hunting and Incident Response
Our work with customers has demonstrated significant cost and time savings by adding ThreatOps tools to these current processes. The most important benefit is reducing the mean times to investigate and recover from incidents. The GIBSEN methodology consolidates and centralizes the entire team's work and provides a detailed map to mitigate the incident, identifies where latent artifacts reside, assigns the right tickets to the right groups, and provides results and reporting faster. As we have seen with new regulatory requirements from the SEC, which now require incident reports within days of incident detection. Other government agencies are also requiring similar reporting timelines, including:
- SEC-listed company regulations (SEC) for disclosure
- U.S. Presidential executive orders (EO 14028) for enhanced cybersecurity
- Supply-chain rules (CMMC) to qualify secure vendors
- ISO 27001 operational demands for (STAR) Level 2 certifications
- Similarly, more from the EU, Japan, and other leading government organizations will demand new training, technology, and reporting
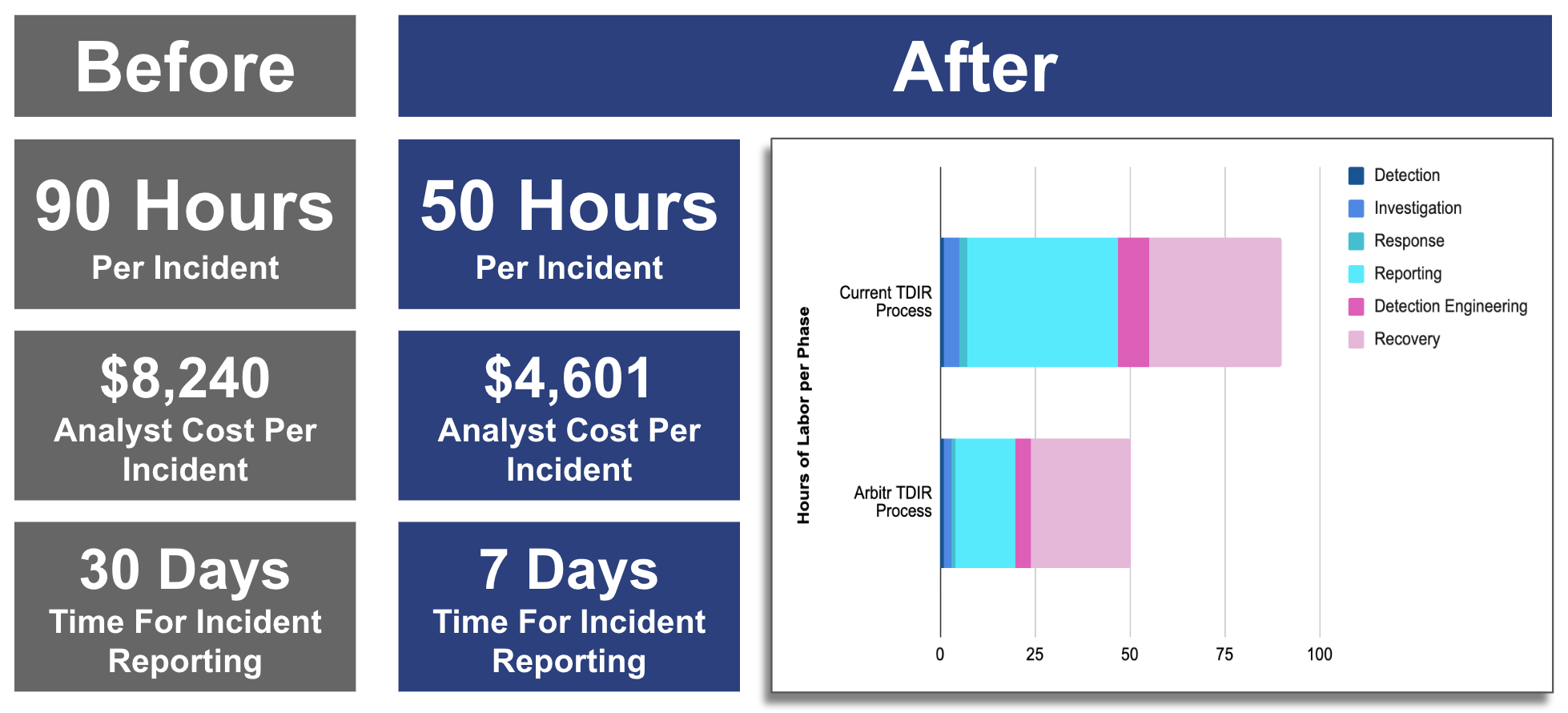
The chart below shows the results for an F2000 cyber team after implementing Arbitr. The key for them was the GIBSEN mapping of the incident, which was populated as each step in the incident was discovered. They credit this automated documentation for improving collaboration and reducing the time to produce complete incident reports. They also said the executives and managers found it helpful to follow the progress and made them feel they better understood the process and results.
Wrapping it Up
At the end of the day, CISOs and cyber teams face a never-ending series of threats and incidents that require investigation. We aim to make it faster, more efficient, and simpler to address these repetitive tasks for cyber teams.
- 50% cost savings on incident response staff costs
- 60% faster incident response or threat-hunting investigations
- 70% speedier governance reporting for executives, boards, auditors, insurers
- Maximize cyber stack ROI via TTP algorithm integration
